Cyber Analytics
Overview
Organizations and IT professionals have become very skilled in protecting themselves from external Internet based threats. Recent security breaches have commonly occurred within the informatics environment of organizations. The experienced professionals at the KTL Group of have packaged a series of tools, methodologies, and processes to quickly monitor and act on security threats.
How it works
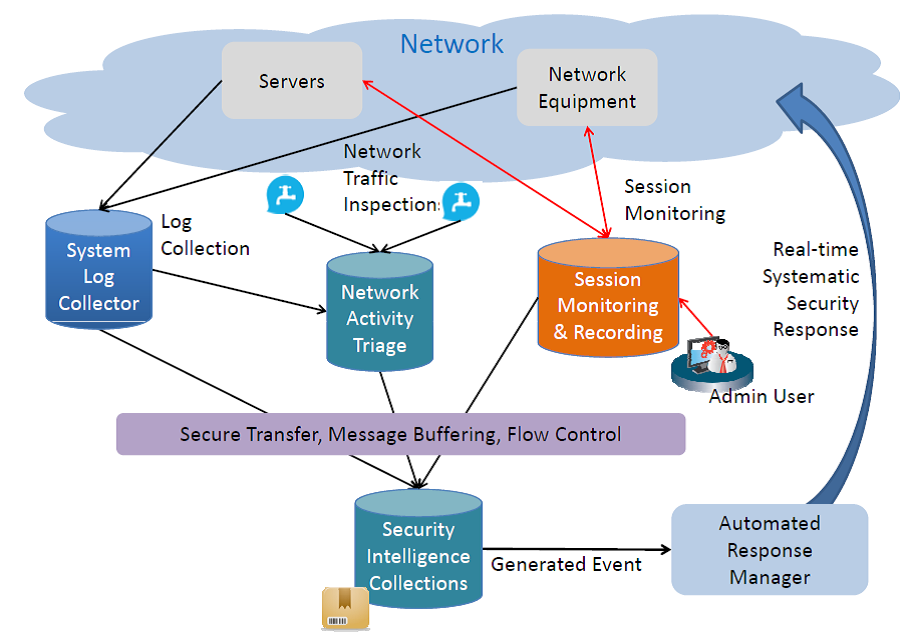
The KTL Group Cyber Analytics solution monitors real-time activity to the servers that house sensitive information and can detect anomalies. In the event of suspicious activities, the Security Analytics component can systematically shutdown access to the monitored resource immediately and alert the IT security teams. All pertinent information is logged and accessible in order to quickly provide a replay of all suspicious activities. A centralized security repository is used to collect, normalize and correlate information collected. Contextual insight and model analytics are used to identify potential security incidents where a single item may not be seed as vulnerability, however a series of collective accesses from unauthorized workstations or users may pose a significant potential breach.
The result
The IT security team has access to network traffic, recorded activity entered in the console, commands, session details, system logs, and source information. All these items assembled can rapidly assemble a clear storyline of the situation in a reliable tamper-proof record, where finger pointing can be easily eliminated. As a result, the IT security team will be able to assess the incident and apply necessary actions without loss of corporate data.